When we think about software, it is customary to imagine that its creation process is based almost exclusively on the process of writing its code. However, we must remember that for the correct, efficient, and secure software production, we need to create a process called the Secure Software Development LifeCycle.
You can also listen to this article:
Over the years, several SDLC models have emerged, such as waterfall and iterative, to more recent agile models, which increase the speed and frequency of deployment.
The intention of the Secure Software Development Lifecycle (S-SDLC) is to allow, through a set of structured security activities, for applications to be developed based on the best practices of secure development – which at the end of the process would deliver us a more secure application.
Check out both models:
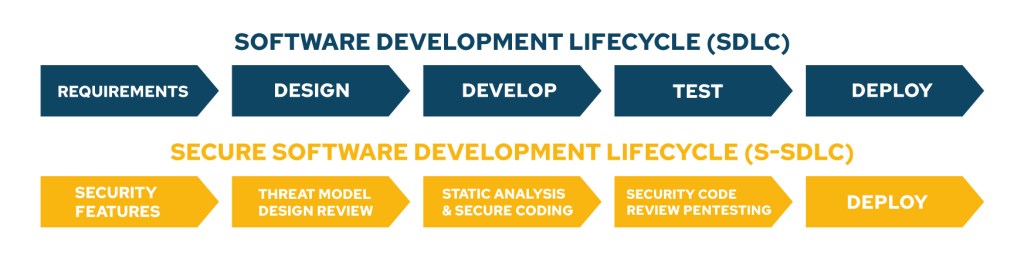
S-SDLC involves refitting existing processes, implementing new tools, and, most importantly, driving a cultural change across multiple teams. Security is an essential part of any application. It should be applied at all stages of the process, helping to prevent problems before they manifest themselves as security issues in production.
The Tools in the SDLC are essential, but there are other solutions to the problem. We jointly execute automated and manual tests, ensuring that security, operations, and development teams work together toward the same goal.
Another critical factor is understanding that testing early and often is the best way to ensure your products and the SDLC are secure from the start. This means teams should start testing in the early stages of development.
How to secure S-SDLC?
Ensuring SDLC security requires focusing on how the application operates and how developers translate security and functional requirements into application code. Security should be part of the teams’ activities as the application is developed. This may require a cultural shift within your teams, but in the end, the result will be very positive.
One of the possible solutions within a scenario of searching for an S-SDLC is structuring an Application Security Program.
An Application Security Program can structure, in addition to the entire process, the way the teams will be trained, how they help in the construction and maintenance of the process, and more. Implementing a Security Champion Program can act as one of the solutions and help generate a complete security framework for the applications.
In general, the SDLC includes the following phases:
- Security Requirements: Ensure that during this phase, the security requirements for the application are identified;
- Design: Apply secure design and threat modeling every time, understand software architecture needs;
- Development: During the development phase, teams need to make sure they use secure coding standards, developers also need to be mindful of the security requirements that have been identified;
- Testing: Should include security testing, using automated tools and manual testing to improve application security;
- Operation: Even after deployment and implementation, security practices need to be followed during application maintenance. Products need to be continually updated to ensure they are protected from new vulnerabilities and are compatible with any new threat scenarios.
Basically, the purpose of the S-SDLC is not to completely eliminate traditional security checks such as a Pentest, but rather to bring security into the scope of developers’ responsibilities and empower them to build increasingly secure applications.
In conclusion, achieving an S-SDLC requires organizations to adopt an up-to-date set of security practices and processes in addition to a DevSecOps approach.
References:

