It is increasingly common to see that companies are projecting their solutions to web applications, transforming their business to be more digital and showing the importance of what is no longer a trend to become a market requirement.
This is a great leap forward for everyone to have access to services and products that would often be difficult to find outside the Internet. However, we have to remember that our applications will be exposed, and thus susceptible to harmful access.
It is common to see flaws in web applications that would be easily corrected in a structured development process and if they had taken security thinking correctly implemented from the beginning.
And here is an example of what will be presented in this text.
The Flaw
In March, it was reported that a company of automatic payment solutions had about 1.6 million data leaked and offered in data sales forums, which may have yielded the criminal approximately 2 million, which could even be paid through digital currencies, such as Bitcoin.
Apparently the flaw used to access the data is related to the authentication breach, which was described in the OWASP vulnerability report, OWASP TOP 10
This Broken access control, when vulnerable, allows users without proper privileges to access data they normally should not have.
With this vulnerability exploited, it was possible for the attacker to have access to data that should be kept secret because it is sensitive data and therefore of great value to criminals.
According to the company, this would be normal behaviour since the access for these queries would be through an API – an interface that allows communication and obtaining data – made publicly available for its partners to have access.
However, the continuity of the communiqué reinforces that there has been a failure in the API authentication process and ensuring the security of these components is extremely important, as it is confirmed that in order to have access to data, the partner needs to be authenticated.
The point is that failures of this kind would be easily identified in secure development processes, with security validations properly structured in the process pipeline.
Possible Correction
The authentication process should be strongly based on an access control policy and it is a basic recommendation that before this component is implemented, the development team should evaluate all the controls that should be done.
It is recommended that when building this policy a matrix is created that indicates how these controls will be implemented and to whom access will be given.
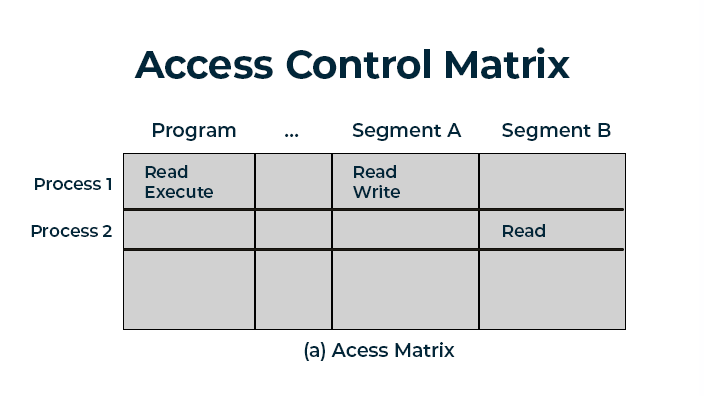
Imagining that the process has already been created and implemented in the application, tests and validations during the development process could identify flaws, which by using a well structures vulnerability management process would facilitate the correction process.
Far beyond the points of code validation, there are other points that would help this problem. Performing Threat Modeling or even the presence of Security Champions in your team, for example
All these points are important and the constant training of the development team is one of the main points that must be observed by any company.
However if we forget all the technical aspect and focus only on the legal aspect, it is clear that the financial impact to the company would be extremely high.
The GDPR
In Brazil, there is already a legislation regarding data exposure, which allows lawsuits for moral damages.
But in August 2020, the legislation that will deal directly with data and privacy comes into force. The General Data Protection Regulation (GDPR), will bring a series of new points that must be observed by companies, one of these points being the one that determines the value of R$ 52 million or 2% of the billing for cases of data leakage.
Taking this as a very close scenario, we believe that it is much more practical, cheaper and efficient to invest in Application Security, using platforms and specific knowledge to help companies in this process.
We hope this text can open the eyes of many managers who still believe that security in web applications is just the execution of intrusion tests in a simple and sporadic way.
Security as a Continuous activity
We have already addressed in this article the impact that neglecting Appĺication Security, or even mismanagement of it, can have on companies. And it was precisely that because of knowing the main challenges in Application Security that Conviso created Conviso Platform, a platform that supports the entire security cycle in software development and vulnerability management.
With this, security ceases to be a bottleneck and becomes a continuous activity, integrated to the whole software development lifecycle, with the right analyses running at the right time, within the best practices and, above all, without reducing the speed of the company’s progress.
Read all of our articles on Conviso Platform

